OIDC
Graylog 4.2 introduces generic OpenID Connect (OIDC) authentication on-premise, ensuring your Graylog login may be managed with a variety of OIDC-compliant identity providers.
Identity Providers and Graylog
These providers have been tested successfully with Graylog; however, you are encouraged to explore authentication with any OIDC-compliant provider that best fits your needs and environment.
Configuration
To begin, you will need to obtain authentication credentials from your provider to configure your OIDC protocol. Navigating each provider’s application will be different, but for this example, we will look at how to set up an OIDC service with Auth0.
Auth0
- Log in to your existing Auth0 dashboard; here you will need to create an application for Graylog.
Note
If you have multiple Graylog instances, then you will need to create separate applications in Auth0 for each Graylog instance.
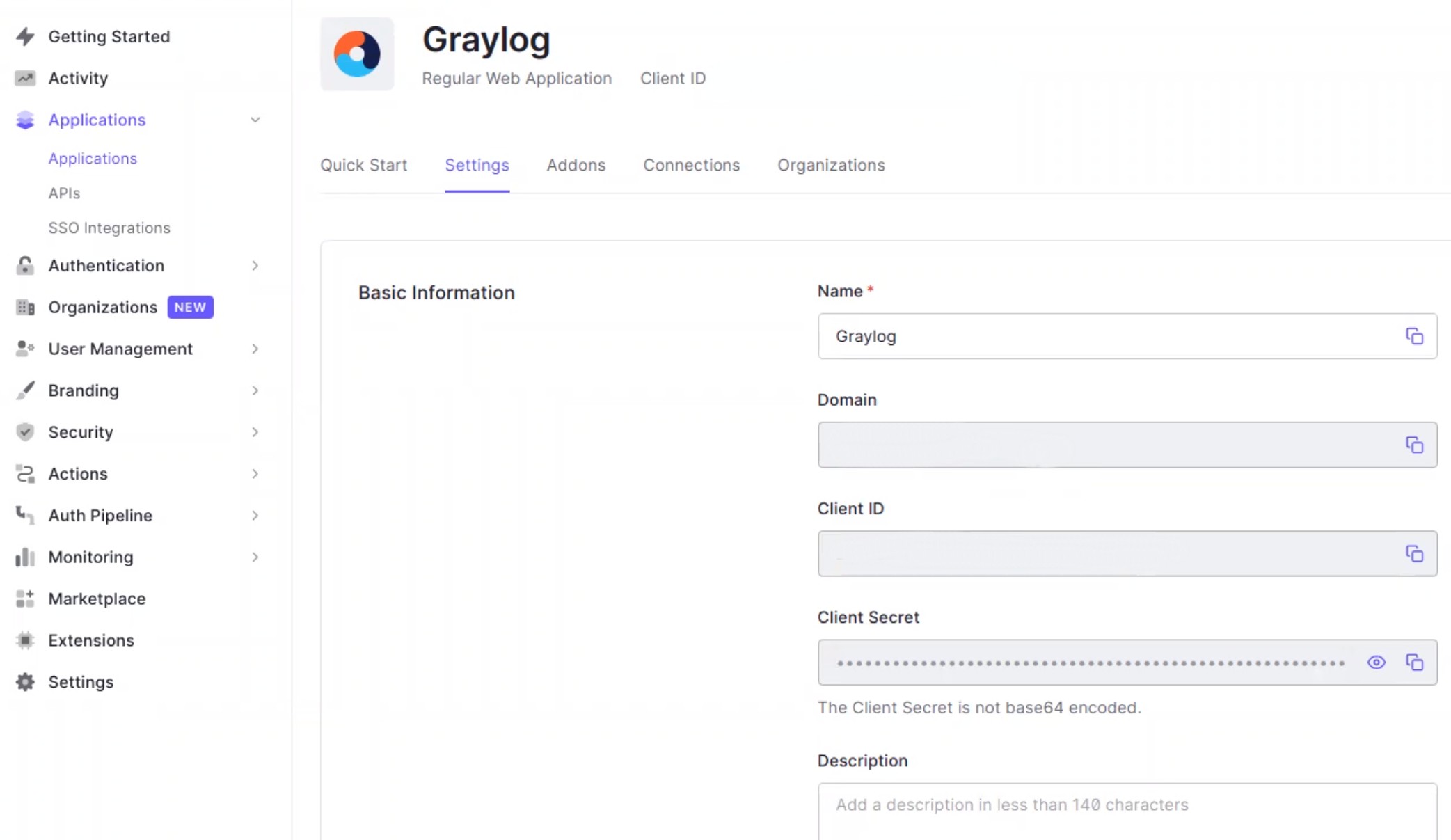
- Once the Graylog application has been created, select this application in Auth0 to view your client credentials. These credentials will be required to configure your OIDC service in Graylog.
- Then, in your Graylog application, navigate to the Authentication page and select Create Service.
Now you can use the credentials from Auth0 to fill in the following fields and make your selections, including:
- Title
- This will be used as the title of the login screen when your users sign into Graylog via your SSO protocol.
- Description
- This field is optional and can be used to provide a general description of the identity provider selected.
- OIDC Base URL
- This refers to the base URL of your OIDC environment and may be obtained from the credentials provided by Auth0.
- Callback URL
- The callback URL will be generated by Graylog beneath this field.
- Client ID and Client Secret
- Both of these values will be provided in the Auth0 application.
- Token Verified Connect Timeout
- It is recommended that the default value of “10” be selected for this field.
- Default Role
- The default role will populate as Reader; this will be the basic level of access needed for most Graylog users and is therefore the recommended selection.
- Title
Finally, you will want to select “Server Connection Check” before applying the configuration. Selecting this operation will allow Graylog to perform a basic consistency and connectivity check of the configuration. Any errors detected at this point will be noted by the application before proceeding.
Group Synchronization
Currently, Group Sync is only available with Okta authentication.
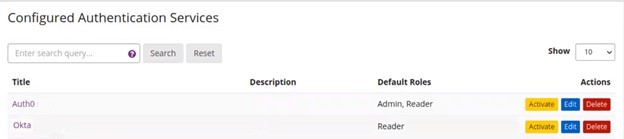
Activation
Once you have configured the service, be sure to activate your current service provider to enable the authentication protocol. Only one authentication service may be activated at a time for each Graylog instance. If you change or service provider or need to update your settings, then be sure to activate the new service from this menu.
Login
Now you will have a new way of logging into Graylog.
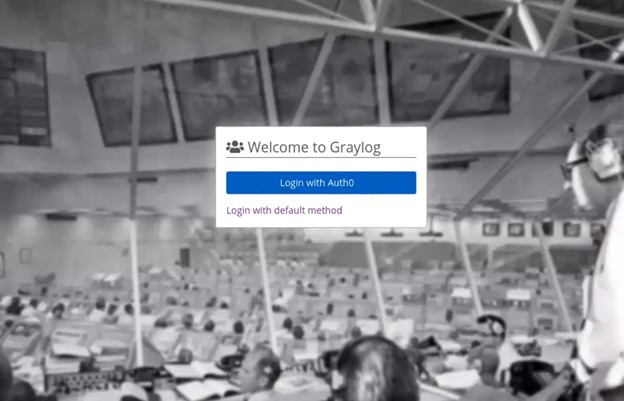
Selecting “Login with Auth0” will take you to the provider’s application to complete your sign on to Graylog.
Note
If you have any issues with your identity provider, remember that you may always log into Graylog using your default admin credentials by selecting, “Login with default method.”