Search Features
Graylog 4.2 introduces enhanced search-related security content features, allowing you to integrate security tasks more seamlessly into your log management.
Prerequisites
Users will need a security license and to install Illuminate.
Background
Once logs are ingested and normalized, they are assigned a code. The Illuminate core schema then maps that code to the following key fields: gim_event_category, gim_event_subcategory, and gim_event_type. This allows for logs to be classified according to the values input into these fields, standardizing the contents of the logs and, ultimately, the way that this information is then presented in the log message.
In 4.2 we use this classification to streamline the search function, allowing you to find the most important information within a message, identify whether a message indicates a meaningful occurrence (e.g. a threat), and proceed with aggregating and analyzing the relevant data.
Message Summary
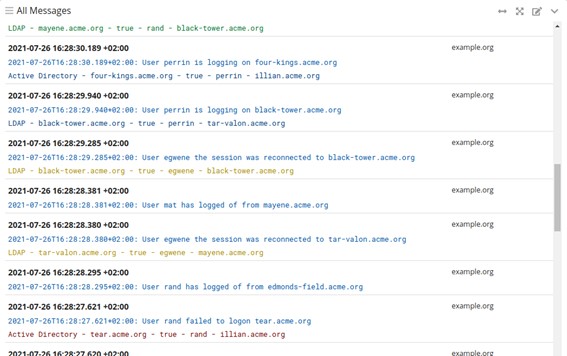
For log data Graylog displays an easy-to-read message summary in the default view of the search pane. This summary is composed of the most relevant information crafted by the Illuminate schema and organized in a logical manner. Additionally, these messages are color coded according to message priority so that the user can begin to visually interpret the data upon cursory inspection.
Note
If a summary for a message exists, it will replace the default message row.
This option is activated by default and can be deactivated when editing a message table widget by deselecting “Show summary.”
Value Actions
Graylog 4.2 also introduces relevant value actions to fields, further expanding ways to use your log data. For normalized fields like source_ip or hash_md5, a drop down menu will display context-specific value actions. This menu can be found by clicking on a message’s field value in the message table widget.
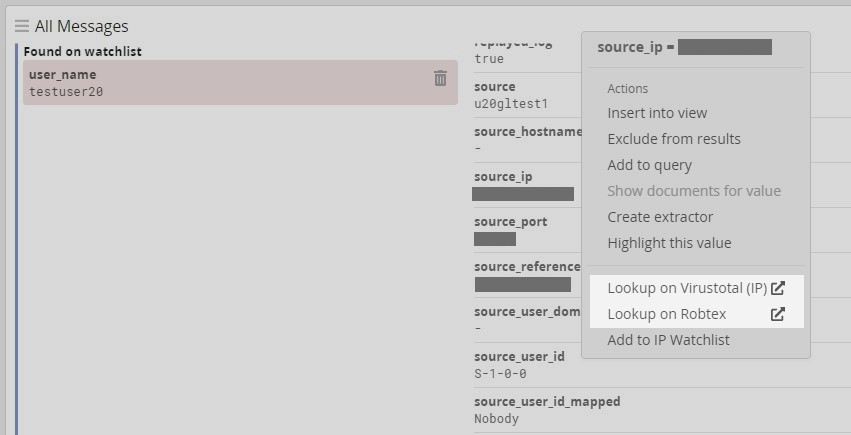
Like in the screenshot above, for an IP field, the actions “Lookup on Virustotal” and “Lookup on Robtex” may be selected by the user for the indicated value.
Watchlist Enhancements
Also included are watchlist indicators embedded in the log message. When a message contains a field value that is on a watchlist, an indicator is displayed within the details of the message. The indicator also allows the user to remove the value from the watchlist.
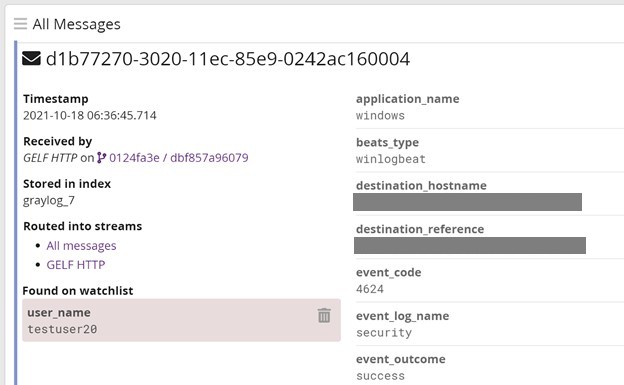
Additionally, qualified fields can be added to a watchlist directly from the log message. The “Add to” and “Remove from” watchlist actions can also be found by clicking on a message field value in the message table widget.
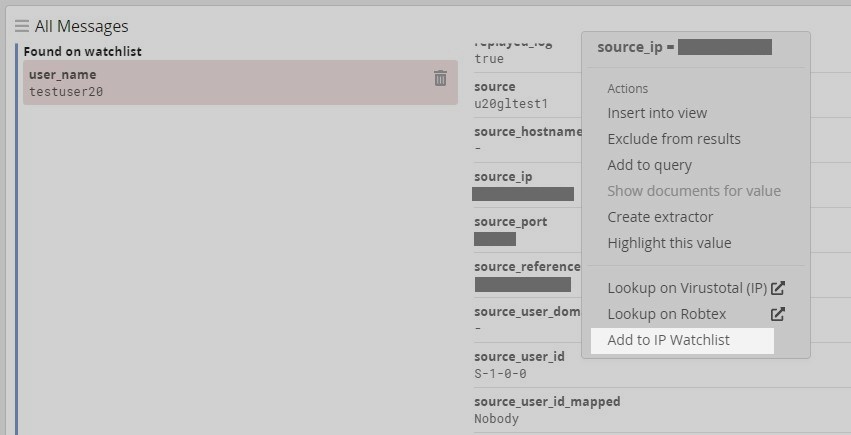
All existing watchlists will be available as part of a watchlist lookup table; these lookup tables will be created automatically when updating to 4.2. Because watchlists are based on a lookup table, they can also be included via a query parameter in a search or event definition filter query. It is also possible to create a pipeline rule that considers entries on a watchlist, like:
has_field("username") && watchlist_contains("user", to_string($message.username))
Note
You will need to verify in the log data that a field exists before its value may be checked on a watchlist.